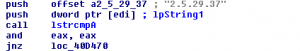Ever had one of those Rogue-AVs or Fake-AVs or know someone who had? Not so bad you think? Read on and think again 😉
So, two days ago I got called by an employee of one of our customers. He said he was searching the web for an explanation of a word and since then could not use his computer anymore because trying to start any program would result in a popup telling him that his software was infected by a variant of conficker. I headed over there to take a look at his computer and what I found was this:
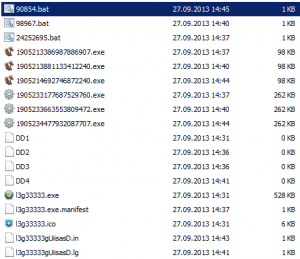
The one that was causing the popups was
l3g33333.exe – MD5 96a8901b0ff0c49bbb7bf9b5221f1399
But what caught my eye were the other 6 binaries in that folders:
1905213386987886907.exe – MD5 a20ad23e771da6c10554f3410b91439d
1905213881133412240.exe – MD5 a20ad23e771da6c10554f3410b91439d
1905214692746872240.exe – MD5 93018c83adf8b4ea6067e791a33f82e4
1905233177687529760.exe – MD5 4bafa135003d6843ba3b87c1dbdc8901
1905233663553809472.exe – MD5 4bafa135003d6843ba3b87c1dbdc8901
1905234477932087707.exe – MD5 4bafa135003d6843ba3b87c1dbdc8901
Needless to say I took a sample to examine the binaries and the first file I examined was 1905213386987886907.exe. The file was compressed using Mystic Compressor. I unpacked the file manually and started to examine the unpacked PE with IDA freeware and here is what I found.
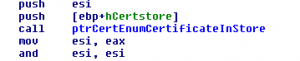
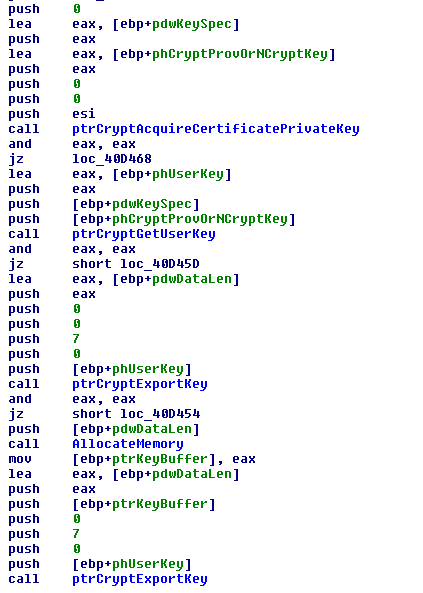
The sample harvests passwords from all common and some not so common software like ssh-clients, ftp-clients, email-clients and webbrowsers. It also tries to collect certificates with OID 2.5.29.37 which are usable for code-signing, and client- and server-authentication and tries to export their private keys from windows certificate store.
The sample also contains a list of passwords possibly already harvested from other victims. The password list is used to try to logon as other users in Windows Terminal Server and Active Directory environments and also harvest their passwords and certificates. The collected data is then sent to a server using a POST-request to hxxp://115.47.49.181/xSZ64Wiax/ojXVZBxRQVfp6gAUziCGnB8V7Aikbs0Z.php.
I did not take a too close look into the sample, just the parts that immediatly caught my eye. When you caught this one there’s a really high chance that all your credentials (passwords and certificates) are gone and need to be changed asap.
I will examine the other samples in the next days to check out what they’re up to.